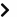Whatweb
Whatweb identifies websites. its goal is to answer the question, "what is that website?".
Dns lookup
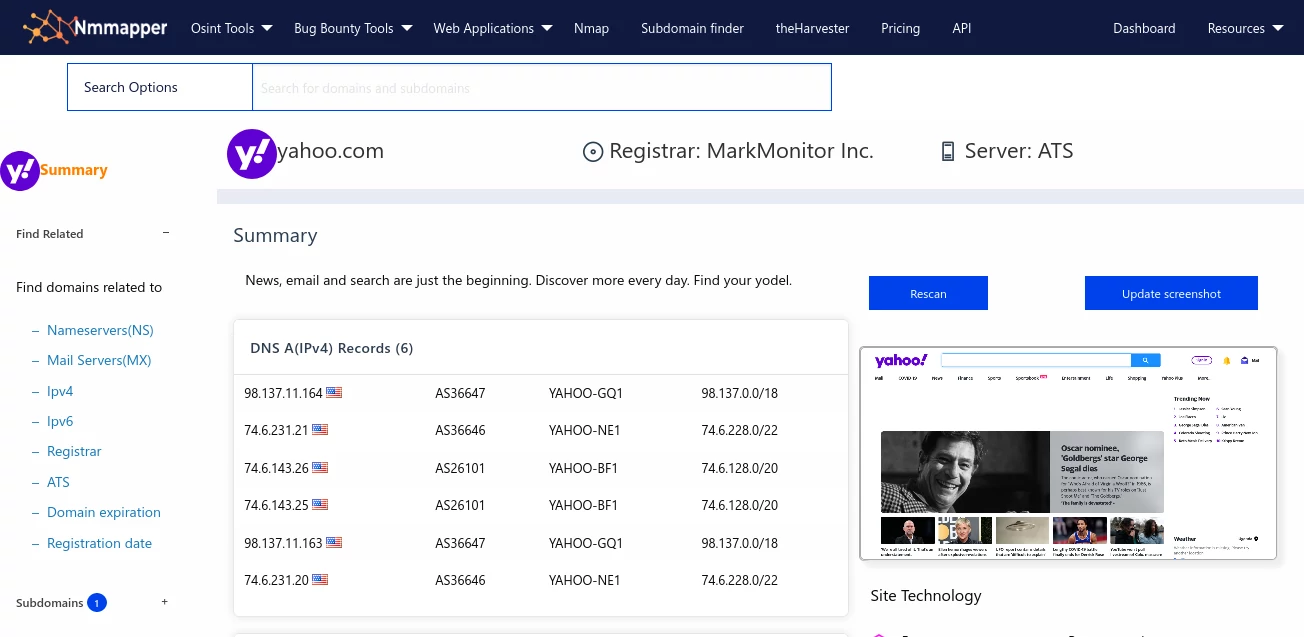
Nmmapper provides dns lookup tool to let you check all dns records of a domain.
Raccoon scanner
Raccoon is a tool made for reconnaissance and information gathering with an emphasis on simplicity.
Cmseek
cmseek is a cms detection and exploitation tool,capable of scanning numerous content management systems.
WAF detector
Web application firewall detection discover the security protecting your target.
DNS reconnaince
Dns reconnaisance is part of the information gather stage of penetration testing.